Verisys FIM
Simple, specialised file integrity monitoring for Windows, Linux & network devices
File Integrity Monitoring
Detects and notifies of changes, meeting PCI DSS requirements 10.5.5 & 11.5, as well as applying to SOX, FISMA, HIPAA, NERC CIP, CoCo and more
Compliance
Get started in minutes with our operating system and application templates for common system configurations
Change Control
Automate integrity checks that notify, report and respond when discrepancies are detected
File Integrity Monitoring
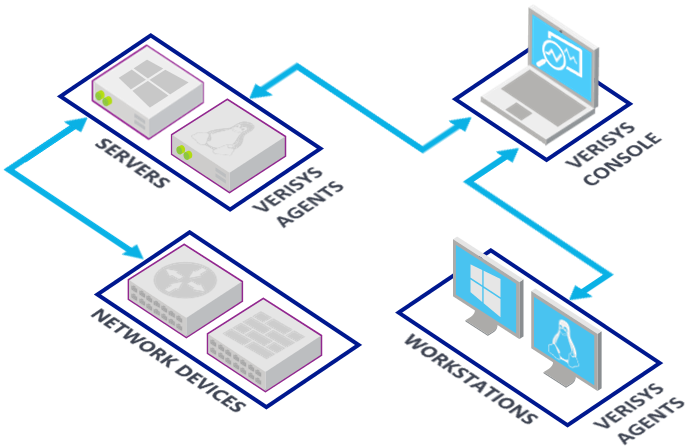
Verisys FIM gives you the ability to detect changes to system objects and network device configuration, ensuring your systems remain in a known and trusted state.
-
Detect Changes
Detect changes to Windows and Linux files, Windows registry objects and network device configurations
-
Alert and Respond
Automated alerting means your key personnel will be rapidly alerted when discrepancies are discovered
-
Reporting
Clear, concise reports at different detail levels in a variety of formats. See a sample
Reduce Risk
Unmonitored systems may be at risk from unauthorised changes - resulting in operational downtime, security or confidentiality infringements or compliance violations. By implementing Verisys FIM, you can be confident that your systems are in a known and trusted state. The Verisys FIM Console and Agents enable widespread monitoring and reporting of your business systems so that, in the event of discrepancy detection, you can act quickly to analyse and rectify the situation.



Compliance
File integrity monitoring is significant to many regulatory compliance requirements, for example the PCI Data Security Standard (PCI DSS). Even if your business is not covered by such regulation, file integrity monitoring is good business practice as part of a comprehensive data security policy.
“Great product - really helped with our PCI compliance"
SIEM & Log Management Integration
SIEM (Security Information and Event Management) and Log Management solutions are now widely deployed, enabling enterprise-wide threat detection and centralised logging.
Verisys FIM integrates with any SIEM or Log Management solution, seamlessly connecting with your existing security and compliance infrastructure, including QRadar, Splunk, Exabeam Fusion, RSA NetWitness, Microsoft Sentinel, ArcSight, Log Rhythm and more.





Respond Rapidly with Automated Alerts
When suspicious activity is detected it is crucial that you are able to identify the key information and respond rapidly. With automated alerts, Verisys FIM will provide clear, concise reports and notifications showing exactly what has changed.
Verisys FIM also integrates with top SIEM solutions, seamlessly coming together with your existing security infrastructure.
Simplified Management
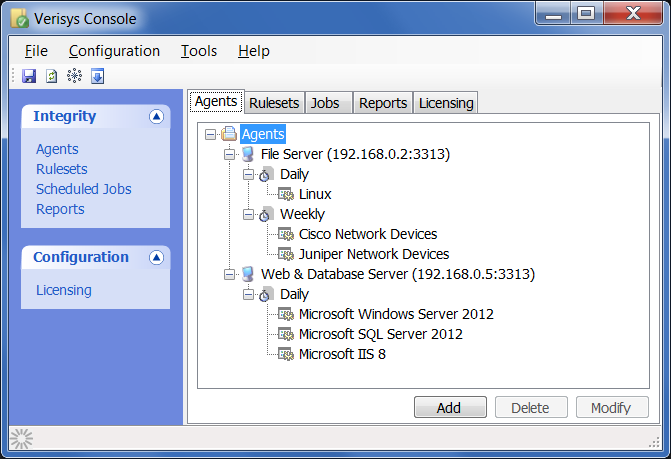
A key component of Verisys FIM is the central administration console, which allows you to configure and control all of the Verisys FIM agents deployed across your enterprise. The central console simplifies the management of large or distributed agent deployments and enables centralised integrity checks, reporting and licensing administration.
Rulesets to monitor servers, workstations and network devices can be configured and published to any number of agents using the Verisys FIM Console, which reduces errors and rollout time, and simplifies the implementation of compliance procedures.
Central Administration
Automated integrity checks can be scheduled from the central administration console including the ability to configure responsive actions to take once an integrity check has identified discrepancies. Integrity checks can also be initiated on an ad-hoc basis, giving you complete control over the integrity of your servers, workstations and network devices.
The console also provides a central point for all your reporting requirements. Using the intuitive interface you can generate reports in a number of formats based on your desired search criteria.
How it Works
A baseline snapshot of the current system state is taken and, according to your configuration, Verisys FIM will automatically compare the system against this baseline to detect any changes. Using the console, you can also start an integrity check manually at any time.
In addition to assessing object properties, Verisys FIM also performs a cryptographic hashing algorithm on the actual data contained within each file - if files are altered in any way, Verisys FIM will detect it.
If files are altered in any way, Verisys FIM will detect it
Trusted by the Defence Industry
By its very nature, the defence industry is often targeted by Advanced Persistent Threats (APTs): state-sponsored, shadowy threat actors that typically use zero-days and unsignatured attacks to gain unauthorised access to networks, where they often remain undetected for extended periods.
For over 24 years, the defence sector has trusted us with file integrity monitoring, change detection and system integrity. Verisys FIM adds an additional layer of security that can enable detection of unsignatured threats that have bypassed perimeter defences and antivirus.









Templates for Rapid Deployment
Verisys FIM includes a library of operating system and application templates for common system configurations, so you can get started quickly and easily.
- Microsoft Windows Server Editions
- Microsoft Windows Desktop Editions
- Linux
- Microsoft SQL Server
- Microsoft IIS
- Apache HTTP Server
- Cisco IOS
- Cisco IOS-XR
- Cisco ASA
- Juniper Junos
- Palo Alto PAN-OS
- F5 BIG-IP LTM TMOS